Chinese apps are not very stable nowadays. Could an app have built has some or other errors followed by the integration of third-party tools? Such technology loopholes impact not just mobile apps but also seriously harm users personal data and economy. Something critical for hardware or software can be some defects here.
Chinese ios apps today are rapidly becoming part of today’s society. Also, it was not evident with the same capacity that the safe mobile app was creating. For the culture, of course, there are sustainable development standards. We’ll summarise here those inconveniences because they’re the most evident in mobile devices.
In our day-to-day lives, Chinese goods, from needles to toys, electronic devices, bottles of hot water, cell phones, TV’s, crackers, car parts, textiles and clothes have become inevitable. Chinese products are sold in India, and significant profits are being transported to China, India’s rival county. As Indians indirectly purchase Chinese goods, the Chinese economy is boosted, and the Indian economy is weakened. The effect of Chinese products on the India economy will be discussed in this section.

1. Poor Authorisation & Authentication
Weak or incomplete authentication mechanisms allow an opponent to execute the mobile application or back-end server functionality anonymously. Due to the mobile device input factor, more inadequate authentication is very prevalent for mobile phones. The form factor actively promotes short passwords often based exclusively on 4-digit PIN s.
Users should be online and authenticate with a back-end server in real-time in traditional android web applications. There are fair expectations in their session that they will have to continue Internet access.
Users shouldn’t always be online during their session in mobile devices. Chinese Mobile web connections are significantly less reliable or predictable than conventional web connections. Therefore, mobile apps can require offline authentication when upgrading. This offline requirement can be profoundly influenced by developers when mobile authentication is implemented.
The most common vulnerabilities are on the server-side. You will pursue the right exercises for web applications. Device identifiers should mainly be ignored for app creation, as devices can be deleted and interacted with. Finally, the out-of-band tokens should not be forwarded to the relevant system.
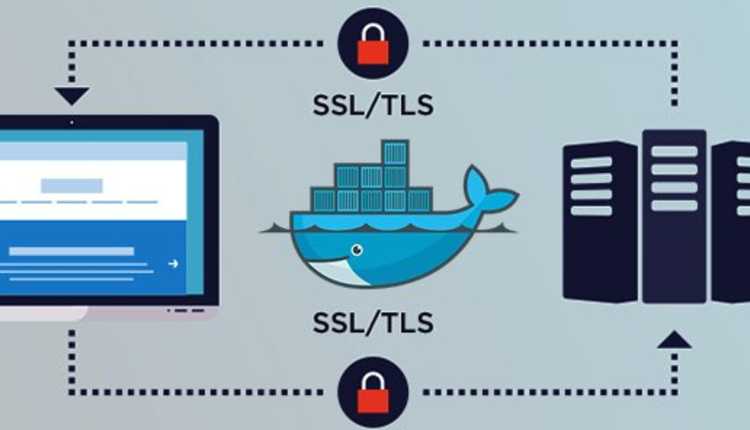
2. Insufficient Transport Layer Protection
What is insufficient security for the layer of transport? It is characterised as the safety vulnerability created by an application that takes no action to protect network traffic. Inadequate protection for transport layers is one of the weaknesses of the web application in which the performance of your platform and specific details needed within your website are definitely impaired.
Apps will use the TLS / SSL during the authentication process. Nonetheless, it is typically not used anywhere in the program, which ensures that the data and session ID are left exposed. In this connection, it is possible to intercept session ID and exposed data which means that the application is vulnerable to any use.
The program also fails to encrypt, authenticate and secure the privacy and secrecy of the insecure network, according to OWASP. Often weak support algorithms do not properly use them and use certificates valid or expired.
Since there are many implementations of the SSL / TLS protocols used extensively across the OWASP, the Inadequate Transport Layer Security is ranked ninth among the top ten threats, with applications such as email, web browsing, Internet faxing, voices over IP, instant messaging and other applications to communicate over the Internet.
Why is inadequate protection of transport layers damaging? By looking at one of the key CRLF attack examples, you can add fake log entries. The insecure program can take unsatisfied or even misrepresented data into the device log file and then write them.
An application that recognises a file name as the user input and does a slightly harmless operation on the particular file can cause further damage.
For communications, you will have TLS / SSL encryption with good algorithms. Encrypted connections between the software and a third-party web development company are a particular error. You will configure your applications to display alert messages so that the configuration of the encrypted link is intercommunicated to the user.
Inadequate layers of transport protection make it possible to expose communications to unreliable third parties to the effects of a web-based application being compromised or to steal sensitive information, in order to provide transport layer encryption. Websites usually use the Protected Sockets Layer / Transport Layer Authentication (SSL / TLS). If the website is configured to use SSL / TLS and is configured to correctly use SSL / TLS, traffic detection and alteration can be vulnerable on the web site.
While session handling mechanisms on the applications server-side are rarely used, secure session management techniques in applications themselves can be used. TLS links can be used to protect the secrecy and privacy of session tokens. Device identifiers such as authorisation & verification should also be omitted here, and secure methods for cancelling session on missing devices should be included.

3. Wrong Session Handling
A web session consists of a network series of an HTTP request and response transactions for the same user. The preservation of the details or status of each customer for several requests is a prerequisite for Modern and Complicated Web apps. Sessions thus offer the ability to set variables, for instance, access rights and localisation settings that apply during the session, to each and every encounter between the user and the Web application.
After the very first user request, web applications will create sessions to identify anonymous users. The user language choice would be an example. In fact, once the user has authenticated, web applications will use the sessions. It means that the user can recognise on subsequent applications and that security access restrictions are enforced, the user can have allowed access to private information, and the program can be made more efficient. Current web applications can, therefore, provide pre- and post-authentication session capabilities.
The session ID (or token) is temporarily the highest authentication method used in the transaction, including the usernames and passwords, passphrases, special OTP password, client-based digital certificates, smart card or biometrics (e.g. fingerprints or retina of the eyes) once an encrypted session has been created.
HTTP is a stateless protocol in which every question and response pair of web interactions is independent. Therefore, to implement the concept of a session, the implementation of session management capabilities is necessary which connect the authentication and access control modules (or permission) commonly used in web applications.

4. Malware
Malware is the common name of many malware types, such as worms, ransomware and spyware. Ransomware for ransomware generally consists of a computer intended to inflict significant harm to data and infrastructure or unwanted entry to a network by cyber-attackers. The malware is typically delivered by way of a connection or an email file which allows the user to click on the link or open the malware file.
Malware is still a threat since the Creeper virus first emerged in the early 1970’s to individuals and organisations. Since then, hundreds of thousands of various malware types have invaded the planet, all in order to inflict the maximum possible disruption and harm.
It is because of the secret identities embedded in the program that many viruses was required to be installed by users. While a Google Bouncer is available in the play store, it can instantly detect and block malware of some kind, but that does not. So developers must test whether or not the program includes malware to ensure a successful product. In fact, there are plenty of free and paid anti-malware applications to shield you from the malicious client.

5. Counter fit Products
There is a lack of resources, industry experience and marketing power for many companies and companies which result in their production of counterfeit products. Several businesses are developing these goods in order to collect intelligence on the success of legal firms such as Samsung, Hyatt and Starbucks. Yet if we look at the situation in the historical sense, it is often argued that this is merely a natural transformation from a low-quality to the falsified development process, which is not exclusive of China alone, since Japan, South Korea and Taiwan have experienced somewhat similar economic phases.


