One of the most prominent and reputed hospitals and medical institutions in the world, AIIMS Delhi, was targeted in a major cyber attack allegedly carried out by Chinese hackers.
According to reports, one of the AIIMS systems became infected with ransomware after an employee opened a suspicious email attachment, which then spread across all systems, including the core servers.
The ransomware encrypted data stored on various computers, including those in the main server room, and demanded 200 crore rupees to decrypt the data. The cyber attack resulted in the temporary halt of all online and offline services.
Government agencies including C-DAC, CBI, NIA, and CERT-In (Indian Computer Emergency Response Team) managed to recover some data in order to resume OPD services, but these had to be managed manually. All services were operated manually until the cyber team could restore the data, sanitize the AIIMS system, and remove the ransomware.
It took several days for the cyber team to scan all systems, install strong anti-virus software, and set up new servers to prevent future attacks. Although the services were restored, the cyber team did not comment on the data breach. As the ransom was not paid, it is possible that the hackers may put the data up for sale on the dark web. This data may contain sensitive personal information about AIIMS officials, employees, and patients.
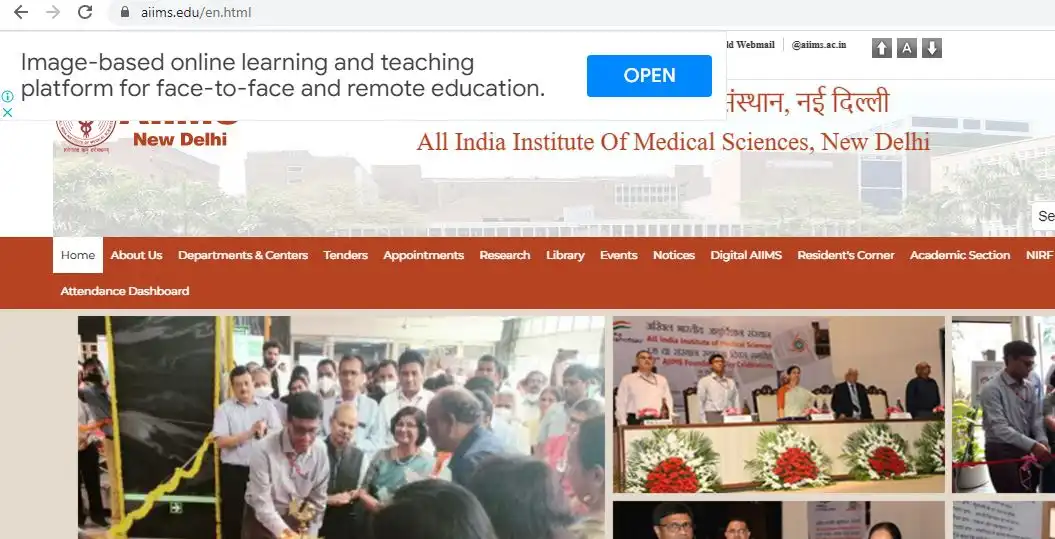
On December 25th, 2022, the founder of Isrg KB, Isrg Rajan, discovered that the official website of AIIMS had been infected with adware. He wrote a letter to the director of AIIMS and informed him of the risks associated with the infection, such as the insertion of malicious code. He also provided information about the source of the breach and offered a solution to remove it.
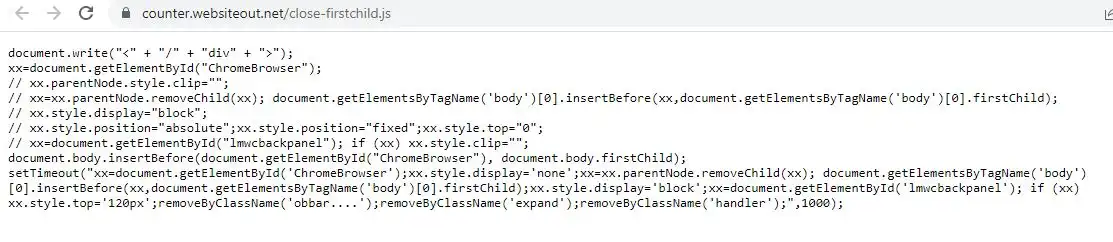
The official website of AIIMS, aiims.edu, was using a third-party hit counter from websiteout.net. Most third-party hit counters typically generate an image URL to display the status, but in the case of websiteout.net, the counter was using PHP which redirected to https://counter.websiteout.net/compte.php?S=www.aiims.edu&C=30&D=10&N=22368976&M=0. It was also loading a malicious JavaScript file from https://counter.websiteout.net/close-firstchild.js (archived here) containing malicious code which could add and load any type of content on the targeted website.
The ads on the AIIMS website included a Google AdSense Publisher ID of “pub-5486891678306037”, which can be found at https://websiteout.net/ads.txt (archived here). In 2021, Google and other advertising agencies made ads.txt mandatory for all publishers. Although the AIIMS website, aiims.edu, does not have any ads.txt files, the website owner, websiteout.net, may or may not be generating revenue from these ads.
However, it is a serious concern that websiteout.net may inject other malicious code, as it is already displaying advertisements relevant to health. This could potentially mislead people and take patients to different websites by following the advertisement. Such a situation could have serious consequences, particularly in the context of healthcare. It is important for the website owner to take the necessary measures to prevent any further malicious activity and ensure the security of the website visitors. The use of unreliable third-party services, such as websiteout.net, can pose significant risks to the integrity and security of the website. As a result, it is crucial for website owners to thoroughly vet any third-party services before incorporating them into their website.
Upon investigation, it was discovered that websiteout.net redirects to websiteout.ca. Further examination of the WHOIS records of both domains revealed that websiteout.net is the owner of websiteout.ca.
This is a cause for concern as it raises questions about the intentions and practices of websiteout.net. If the website is redirecting to another domain, it is unclear what type of information or content may be hidden behind this redirect. Additionally, owning multiple domains can indicate an attempt to conceal information or hide behind multiple identities.
In order to protect the security and privacy of the users, it is important to understand the motivations and activities of the websites we interact with. The discovery of the connection between websiteout.net and websiteout.ca highlights the need for increased caution and investigation when it comes to third-party websites. (WHOIS records archived at archive.org of websiteout.ca and websiteout.net).
After Isrg Rajan brought the matter to the attention of the AIIMS Director and offered his assistance to the AIIMS IT Cell, they quickly took action to address the vulnerability on the website. The AIIMS IT Cell worked efficiently to eliminate the vulnerability, demonstrating their commitment to maintaining the security of the website and ensuring the safety of those who use it. It’s important for organizations to have the proper protocols in place and a responsive IT team to address any security threats in a timely manner. By removing the vulnerability, the AIIMS IT Cell has ensured that the website remains a safe and reliable source of information for all users.